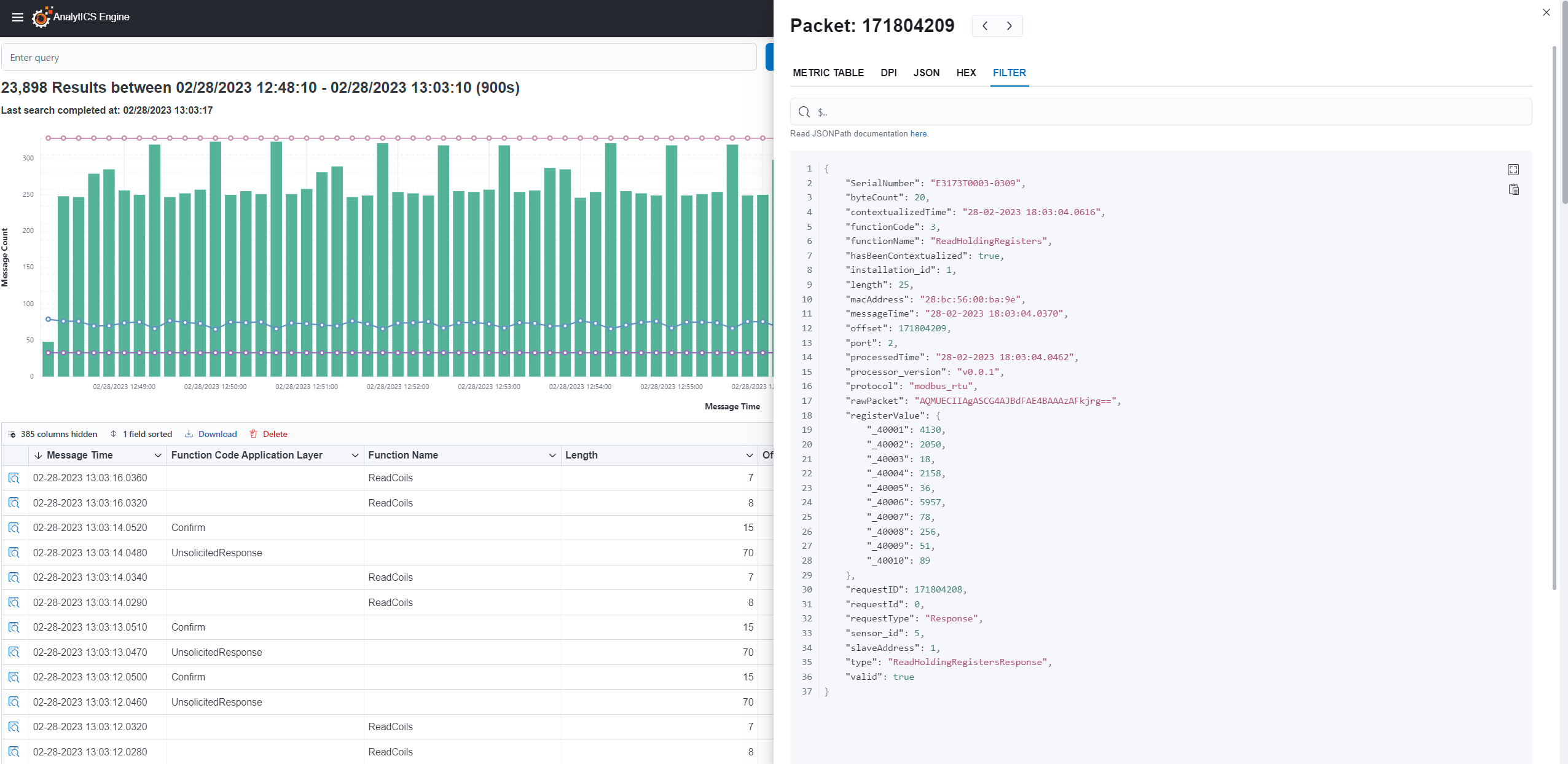
Securing operational technologies (OT) has become increasingly crucial in today’s interconnected world. I am excited to announce that Nozomi Networks and Cynalytica have joined forces to deliver a groundbreaking solution that extends visibility, situational awareness, and threat detection across operational technologies. This partnership now offers the unique capability to monitor both IP and non-IP based ICS/SCADA and OT communications.