In industrial automation, Serial to Ethernet Converters/Gateways and Serial Device Servers are a long-established and widely used method for enabling remote communications and monitoring of devices that only support serial interfaces such as RS-232, RS-485, and RS-422 to name a few. The devices are typically used to convert serial to ethernet protocols (and vice versa) in order to migrate legacy Industrial Control Systems (ICS) networks to modern Ethernet TCP/IP networks and enable interoperability within OT environments. In an age where digital transformation heavily influences critical infrastructure’s initiatives, Serial to Ethernet Converters provide ICS operators with a cost effective and easy-to-use solution to achieve operational efficiency. However, as the ICS threat landscape rapidly broadens, they have proven to be a double-edged sword for asset owners – by presenting malicious threat actors with a gateway to high-risk cyber-physical devices.
Background of Serial Communications in ICS
Serial communications have been deployed in industrial automation since the 1960s and, despite the development of newer digital standards, are still used in ICS thanks to their simplicity and efficiency. Recent industry estimations suggest 30-60% of ICS still rely on legacy serial protocols such as Modbus, Profibus, and DNP3, which were developed in 1979, 1989, and 1993, respectively. These protocols are intrinsically insecure as they were not developed with security in mind and although superseding and more secure serial communication technologies are now available, like Ethernet for instance, industrial automation manufacturers often choose to support connectivity based on RS-232, RS-485, and RS-422 serial interfaces because they are inexpensive and universally supported. Furthermore, many ICS environments still operate obsolete legacy controllers due to the expense and significant downtime associated with replacing them.
Background of Serial to Ethernet Converters in ICS
Nowadays, the standard network communication is routable TCP/IP, which means a significant number of OT networks depend conjointly on TCP/IP and serial communications. Before TCP/IP existed, connectivity to field devices was restricted to localized networks i.e. engineers were required on-site to investigate incidents and carry out network maintenance and updates. While the introduction of TCP/IP helps establish remote connectivity, it cannot be fully achieved within a network that has serial connected devices – this is where Serial to Ethernet Converters come in.
Serial to Ethernet Converters, as the name suggests, connect legacy serial-connected devices to a local area network (LAN) by converting serial to TCP/IP (and vice versa) and enable two way communications for remote access and monitoring. The devices range in security, capability, and implementation, and can be found in any ICS environment that remotely communicates with their serial-connected assets. There are various types of serial-to-ethernet converters such as:
- 1-port models which enable remote connection to a single serial device
- Multiple port models (also known as device servers) which enable remote connection to multiple serial devices
There are also different implementations for the converters based on the serial port’s physical layer (RS-232, RS-485/422, etc) and they are often protocol specific.
As exemplified by the sheer volume of Serial to Ethernet Converters within ICS, the technology brings undeniable value to operators who are attempting to enhance their OT network efficiency and increase productivity – albeit at the expense of their network security.
Network Security Challenges
Legacy serial communications present profound security challenges to ICS as the protocols were devised before modern cyber threats existed; thus, no emphasis was placed on security. Legacy serial protocols do not support encryption and authentication of commands, and are unable to log commands sent to devices securely. Consequently they are susceptible to tapping, interception, replay attacks, malicious and unauthenticated command execution.
This lack of security protection is exacerbated when a routable network device that enables two-way communications is introduced; legacy devices will accept any command from a converter with no authentication of the message due to the security flaws mentioned above.
As Billy Rios (CEO of WhiteScope) said in an interview with Security Ledger entitled Serial to Ethernet Converters are the Huge Critical Infrastructure Risk Nobody Talks About (Paul Roberts April 11th, 2016):
“Once you have access to the converter, its game over.” “The devices attached to it will do whatever you tell them to do.”
This is not to say that all Serial to Ethernet Converters do not have their own built-in security features. Depending on the vendor, some provide more security features than others, but this comes at a cost. Also, the converters with security features are still not entirely immune to exploits and require a degree of vigilance from vendors and operators alike. Over the past few years, ICS-CERT has published advisories relating to several serious vulnerabilities found in Serial to Ethernet Converters – this alone should perturb ICS asset owners.
If a device’s software is not sufficiently patched and updated, it can lead to serious security issues. Astonishingly, a quick search on Google will show an array of security-related incidents such as leaked passwords and vendors‘ inadequate responses in addressing the problems. With that in mind, it’s little wonder that Reid Wightman, director of Digital Bond Labs, told Security Ledger:
“We’ve always told customers to treat these products as if they’re totally vulnerable to anything.” – “I haven’t encountered a serial converter yet that is very secure.”
Serial to Ethernet Converters Roles in Previous Cyber Incidents
Ukraine 2015: On 23 December 2015, the first known successful cyberattack on a power grid took place. Attackers successfully compromised ICSs of three energy distribution companies in Ukraine and shut off power at 30 substations, leaving 230,000 people without electricity for up to six hours. A DHS report stated that the adversaries:
“rendered Serial-to-Ethernet devices at substations inoperable by corrupting their firmware.”
Although it is unclear if the converters in question had any security features, it is evident that the hackers leveraged the devices to achieve their overall goal – which was to exploit the substations’ legacy field devices.
How to Mitigate the Risks Associated with Serial to Ethernet Converters
To ensure safe and reliable industrial processes, asset owners must enforce strict cybersecurity hygiene policies similar to those that follow the relevant NERC/CIP ICS cybersecurity compliance guidelines. It also goes without saying that procedures for implementing security patches need to be strictly observed in order to prevent known vulnerabilities from being exploited. Nevertheless, even with the most observant operators, an ICS is still vulnerable to attack so long as they are using Serial to Ethernet Converters to communicate to their legacy devices. Consequently, it is critical for operators to validate the data along the serial bus to accurately monitor a legacy device’s behavior.
On the back of a string of high-profile cyber-physical attacks, the DOD and ICS security practitioners are now vouching for passive monitoring of legacy field devices at level 0/1 (between field devices and controllers) – ‘Passive’ meaning the appliance cannot write to the line and inadvertently introduce an attack vector to the device it is monitoring. Additionally, level 0/1 monitoring provides a solution to spoofing attacks/false feedback attacks. As seen in previous cyber-physical incidents, adversaries can intercept data points received by SCADA and send false data representing normal operations to monitoring tools while writing malicious commands on the field device. Therefore operators should not trust serial-related data points unless they are tapped directly from the serial line from a secure device.
Passive Monitoring with the SerialGuard AnalytICS Platform
The SerialGuard AnalytICS Platform is purpose-built to mitigate the risks associated with legacy serial communications. The platform consists of a hardware device (SerialGuard) that passively taps level 0/1 serial communications, together with an intrusion detection and data analytics platform (AnalytICS Engine) that enables operators to baseline normal operations, as well as to detect and alert anomalous behavior.

The SerialGuard hardware device is a fully passive and fail-safe sensor that installs in-line between field devices and controllers, enabling it to capture real-time data and provide operators with a spoof-proof approach to monitoring their legacy equipment. The sensor offers protocol-agnostic support for various legacy serial networks, e.g., Modbus, DNP3, Profibus, BACnet, and is configurable to accurately frame all the bytes into messages even if the data it captures is unknown. It also secures the data by encapsulating the captured communications into encrypted TCP data packets before forwarding them to AnalytICS Engine.
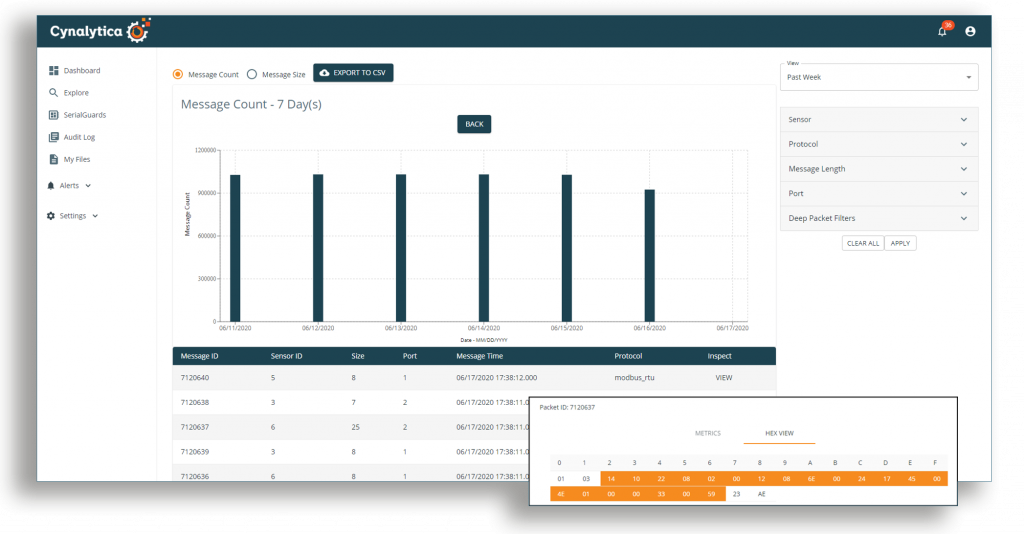
Cynalytica AnalytICS Engine gathers and stores the encrypted serial data packages and performs thorough deep packet inspections to contextualize the assembled data. The software operates as an End Point Protection (EPP), End Point Detection and Response (EDR) and Intrusion Detection System (IDS) and data validation tool by enabling operators to create rule-based alerts to support early detection of anomalous behavior. Its graphical user interface provides visual components and data filters that allow in-depth evaluations of the captured communications. The platform also seamlessly integrates with third-party SIEMs to optimize visibility across the OT network.
The SerialGuard AnalytICS Platform will act as a last line of defense for Serial to Ethernet Converters. The platform’s core tenant is to monitor serial communications at the lowest level of the operational distribution chain, giving operators true visibility and the capability to fully validate the integrity of their legacy devices.
This article also featured on Industrial Cybersecurity Pulse, August 29, 2021